|
Technological advancements have made data transfer to and from aircraft easier than ever. You can work on that document, make that call, play that game, watch that movie, and send that email as easily from your seat in the cabin as from your office, yet more data transfer means more opportunities for hackers.
There were 2,814 data breaches recorded in 2023, resulting in eight billion records being compromised, and the cost of a cyber data breach averaged around US$4.45m, which doesn’t include reputational damage.
Alarmingly, the average time to detect a violation was nearly four months. Fifty-three percent of users do not change passwords regularly, and an alarming 57 percent record passwords on easily seen sticky notes.

NOC at SD World Headquarters.
These stats clearly illustrate that the threat of cyber events is a clear and present danger, yet protocols around cyber vigilance still need to be improved. A serious breach can push a company to a crisis point. Still, we often sense that companies don’t believe it will affect them, so we spend significant time, effort, and investment applying our security mindset to support SD customers’ cybersecurity.
One critical point to understand is that threats are constantly changing. Just as our technology is evolving and we use more devices than ever, malware attacks are rising, with over five billion occurring in the last year. SD blocks some 10,000 attempted malware attacks on our customers’ assets every day.
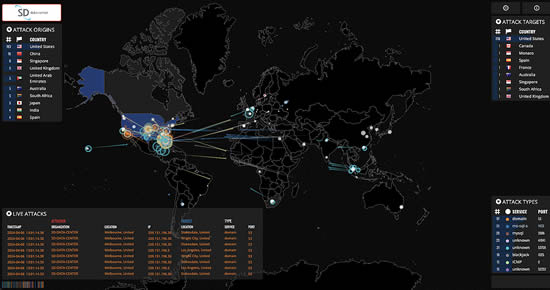
The SD Data Center Attack Map indicates attempted cyber events (88).
[click image to enlarge]
Social engineering is still a common strategy, using cheaply acquired software readily available online to manipulate user behaviour. Many of us are aware of Phishing, the use of fraudulent emails to appropriate this data. Phishing gives rise to clickbait scams, giveaway frauds, false Facebook quizzes and cloned accounts. These remain the greatest threat to operators and rely on simplicity, clever tactics, and slick graphics to trick users out of valuable information.
However, we are seeing increasing cyber events manifesting in new imaginative guises that are moving the goalposts for cyber attacks. Clients often think they are immune because they don’t use a laptop in flight, but this is not the case. If the phone is connected to the internet, which it nearly always is, it’s equally as vulnerable as a laptop or tablet. Phones offer a new platform from which to gather information or direct behaviour.
Smishing, which uses fake texts to extract data, and Vishing, which uses voice-generated AI, are entering the sector. The clever use of AI, publicly available digital recordings, and a little background research can generate convincing fraudulent phone messages in which voices and speech patterns are emulated. These vocal frauds can be extremely convincing.

SD Data Center.
The irony is that even simple actions can make a huge difference, and we continue to encourage customers to employ straightforward tactics to mitigate risk. Using passwords to protect cabin Wi-Fi is obvious, yet flight departments can be reluctant to create Wi-Fi passwords due to the perceived inconvenience to passengers. Passwords can be regularly changed and conveyed to passengers with an easy-to-access QR code. For those generating personal passwords, surprisingly, it is harder for decoders to crack a long password, say the first line of your favourite song, than it is to figure out a short password that includes numbers, special characters and letters.
Think before you connect is another prime hint. It is better to switch off auto-connect and actively decide which Wi-Fi networks to connect to. Stay on the cellular network if you’re not sure the Wi-Fi is legitimate. Make a habit of locking your devices and securing them with a password. If you are given or find a USB drive, leave it alone and in the same spirit, don’t plug your device into unfamiliar docking stations; these are all ways that enable bad actors to connect to and access digital devices. If you travel, use a virtual private network, VPN, for an encrypted connection. This creates another layer of defence when logging on to a hotel or FBO network. Equally, when travelling to a new country, ask your technology department to confirm if it is high risk in terms of cyber events and if it is, leave your data-rich devices at home and carry a loaner device.
As the amount of data transmitted from airframes increases exponentially year on year, we continue strengthening our multi-layered cybersecurity policy that, through a blend of human expertise and advanced technology, protects SD customers. The entry-level offers a vulnerability audit, while the advanced SD Private Network transforms the cabin into a secure workspace by encrypting and routing data to your corporate headquarters without ever touching the public internet. It’s a matter of when, not if, a cyber event will happen. We put cybersecurity at the core of all our operations and encourage our customers to think the same way.